What does labour law have to do with information security?
On the face of it, this question and the title may appear intriguing for the uninitiated labour law (LL in short) experts for whom the Information Security (IS in short) may be a new domain. Presently, among a major section of population, it appears that IS is being perceived as something to do with IT (Information Technology) or controls or audits. The truth is more expansive than this view.
Let us start with a high-level conceptual history of LL. The need, codification and expansion of LL came about due to the appalling condition of workers in various establishments, originally in England, which was the first, apparently, country to formalize “industrialization”. A common thread or purpose or theme, stated or otherwise, of various laws, status, regulations or rules, globally, is, among other things, to protect the rights, provide safety, welfare and security of individuals, thereby preventing discrimination and exploitation.
Long before the advent of Information Technology (IT), data/information security was considered important while dealing with sensitive and/or confidential data/information; however the handling of data/information was more manual. People were aware of the sensitivity and the spirit of maintaining confidentiality was largely prevalent. With the intense presence of IT in every other field now, ‘Information Security’ has gained more significance but poses new challenges due to the proliferation of IT and ease of use in this system.
The global standard and accepted definition of IS is “Preservation of Confidentiality, Integrity and Availability of Information”. Thus security of employee’s information needs to be ensured. A well-defined and implemented Information Security Management System will give confidence towards compliance. Employee’s information comes in two different flavours: Personally Identifiable Information (PII) and Sensitive Personally Identifiable Information (SPII) and both of which need to be secured. Generally, SPIIs are private in nature and thus linked to an individual’s privacy.
In the contemporary context, privacy is an explicit right of individual and that too being considered a fundamental one globally. As far as India is concerned the Supreme Court, in Justice K.S.Puttaswamy (Retd) and Anr. Vs Union of India And Ors. on 24 August 2017, pronounced that privacy is a fundamental right. Thus the privacy of employees needs to be protected in compliance with provisions of laws. A couple of examples: (1) EU’s GDPR is an elaborate and robust regulation pertaining to Privacy and (2) Rule 4 of Information Technology Rules, 2011 (India) mandates that ”Body corporate” shall have a Privacy policy. In addition, a more comprehensive regulation is being considered and planned to be taken up for passing (Data Protection Bill) by the Indian Parliament.
Any ISMS (Information Security Management Systems) designed and implemented to secure and protect individual’s information thus should ensure those information aspects of and individual’s Privacy right are upheld. A robust ISMS would not only ensure privacy rights of employees of an organization, but it will also secure the privacy of all individuals (eg: contractors, vendors, client, visitors) whose information the organization collects, processes, stores, or transmits. In addition, to protecting information and privacy, ISMS will prevent misuse or overuse or exploitation of an individual’s data/information.
With regards to requirements or controls of an ISMS, all aspects discussed above can be grouped under legal, and statutory obligations, which is only one of the many possible requirements and controls. From the IS definition, it may be clear that other aspects of organization business, including but not limited to Operations, IT, ITES, HR, GRC, Marketing, FIN, are to be factored in. For example, if one looks at the ISO 27001, which is the international standard for ISMS, it lists 114 controls covering the entire spectrum of functions of an organization. A pictorial representation of the composition for illustration purpose is shown below:
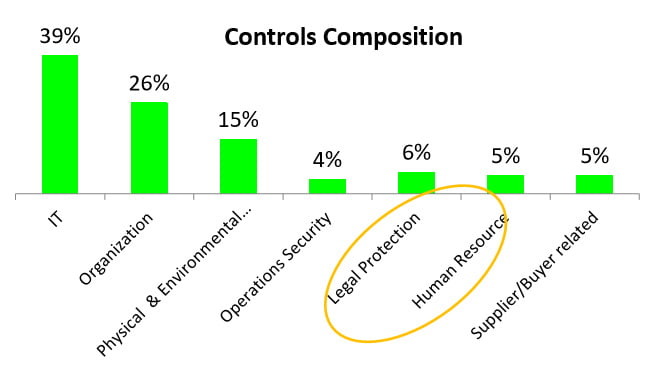
From the above, it may be inferred that various stakeholders (including government) involvement need to be taken care to have robust and effective ISMS. Due to the entanglement of, apparently, conflicting requirements of the stakeholders there are challenges introduced and those need to be mitigated.
Challenges
In Indian Labour Law context, various category of compliance tasks are to be taken care of by an organization – including but not limited to Registration, Renewal, Remittance, Displays, Register Maintenance, and Return submission. The Information Technology Act, 2000 permits maintaining the documents and records, for the purpose of any law, in electronic form. However, the labour authorities were not warming up to the digital revolution until recently and were reluctant to accept E-files and insisted to obtain an exemption for E-records maintenance.
The third dimension of IS, namely Availability, has a direct link with labour laws and other laws, as well, through the concept of “Statute of Limitation” with regards to retaining information. To illustrate, let us consider a couple of Indian laws. Maternity Benefit Act specifies that applicable records are to be retained for two years from the date the last entry was made; similarly, the Payment of Wages Act requires a retention period of three years. There are other Acts/rules which specify a longer period: Companies Act mentions eight years, Delhi Labour Welfare Fund Rules specify 10 years.
As for making the information available is concerned, there may be possible conflicts with regard to ensuring compliance. For example various LL regulations mandates making the wage registers available to public authorities but in many conventional and contemporary organizations there is a salary confidentiality policy. This introduces challenges as the salary to be made available outside the organization in contravention to internal policy. Hence while defining the “Availability” or “Retention” in ISMS, the statute of limitation and applicable statutes and rules need to be appropriately considered.
Now the trend and mood have been reversed and the authorities are insisting on digitization. There is a complete push towards E-files and E-governance as can be evidenced through the various LL portals such ESIC, PF and Shram Suvidha portals. This has created challenges for traditional and organization with voluminous records. To fall in line with the digital revolution organizations need to change and revisit their internal processes, and increase IT infrastructure and related expenditure. These changes will come with their own risks for information security.
Summary:
To summarize, it is clear that Information Security has touchpoints with all the aspects of business and operations of an organization, not just with IT, which, of course, is a major player. With regards to Labour Law considering Information Security is the need of the hour going forward…QED.
Dr. S.Venkatesh
subba.venkatesh@aparajitha.com